Winja - C0C0N 2020

Winja CTF is a initiative by nullcon. CTF was beginners friendly and it was easy and intermediate level. We had different levels of challenge and submitting any one flag of current level will reveal the next level of challenges. At end of the day it was the Amazing CTF, Follow up for the full writeup of the CTF for each challenge. Some Challenge it did not solve during the event, but one it was open for writeup and pratice I completed them.
LEVEL 1

The did not have any long description only website link and even after looking into the website it didn’t have any interactive session to break through. So went for directory Bruteforcing as common for all website challenge.

btw we got the directory called /flags, Fortunately this was the first challenge in 1st level we have two flags for this and upcoming next challenge of same version.
This challenge is continous of previous challenge, where we got both flags already at /flags directory, you just need to copy paste other flag here.

From name of the challenge and filename which was given I taught it exe file would format the C drive and this was bat script. So download and checked the Filetype but we got ASCII Text type. Then lets try strings to print all printable characters from the compiled program.

There you go this wasn’t a compiled program and part of c program was there when you stringed out the given file.

Next challenge, As usual this one was given with web link but name and url is kind of fishy, which denotes like binary exploitation but which weren’t the flag for the solution for this challenge. Visit the page it had login panel, after trying the default credentials, it didn’t accept then taught of looking into the source code, we had you Javascript file with bof.js and bo-temp.js.

On looking into bof.js, we weren’t able to figure out useful bypass technique even it didnot have anything related to the flag. But bo-temp.js which were used for login validation and which had the flag in source code you would typically copy paste.

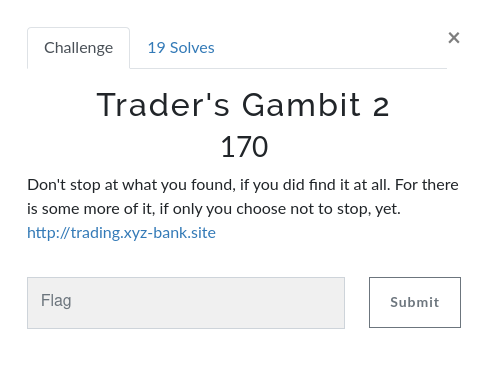
Here we have another part of previous challenge but we were given with different url this time. On visiting the page we had same layout but instead of login panel we have field to check whether flag is right or not. Like previous challenge we had two javascript file flag.js and flag_script.js

In this challenge also the flag was in clear text at flag.js, but we had part1 and part2 you have to concatenate both and submit it.

Here we have a different challenge, and we was given with tar file and description says its encrypted we have to break it. On extracting the file we had 2 jpeg images and 1 encrypted file .

Here we have 2 jpeg image which is valid format for steghide, but before that lets look in the metadata of the file using exiftool for alcohol.jpg

We get information that it was encrypted using futureboy.us, so now its clear we have some steghide data hidden and comment say the password for it. but which was the password for that steghide. On extract steghide data which does not need any password we get the same password. Lets inspect on another jpg image file. On the same we had steghide without any password.

Now we have private key and password for private key and encrypted file, on guess this should be encrypted using openssl with rsautl. But on decrypting it shows some error related to data, which is not right. After taking a look at the encrypted file it was in base64 formated, which was the problem for this and I decrypted and stored in a different file and repeat the process, and here we got it.


One of the cool challenge in Level 1, We have a csv file with a lots of random numbers and Description is also tricky. During the event I could not figure how to solve this and after that with a small hint from author : Use google sheet with filter. Which was the key for solution of this challenge.

This is how the file data looks like, there you can find the flag was spread around the rows and columns. But you can see a large number that is different from other column at COL9, Which was the key for challenge. We have to create a new filter and sort the COL9 and you will get the flag.


Here comes a interesting one, we have a ova virualbox, we have a debian 10 machine but we dont know any login credentials for getting into it. After looking into the challenge name and description it was related to the File Transfer Protocol (ftp) service which would be running in that machine.

As we taught it was ftp service which was ProFTPD 1.3.3c which was running at port 21 and this was a old version and connecting to it we have another information through banner, service was running with default installation.
ftp 192.168.1.104
Connected to 192.168.1.104.
220 ProFTPD 1.3.3c Server (ProFTPD Default Installation) [192.168.1.104]
Name (192.168.1.104:aravindha):
331 Password required for aravindha
On searching for the exploit, we have backdoor for Command Execution from rapid7 and it had metasploit module. Check [here](https://www.rapid7.com/db/modules/exploit/unix/ftp/proftpd_133c_backdoor). But on trying out the exploit which didnot work for me properly, they after long time I found it was problem with my payload and switch to peal script and got reverse shell with root access.

Here to unlock the next level you have use one of these Level1 flag to get access to next level which of really cool.
Level 2

In this challenge we were given with file with name this_is_a_binary and challenge name say its liar liar which match when you check for the file type and it was HTML document.
file this_is_a_binary
this_is_a_binary: HTML document, ASCII text
On strings of the file, we got the source code of the html file which had a image file with base64 string into it, which was only thing out of the file. on Decrypting it we get a hexdeciminal value and converting it to ascii we get the flag.
echo "dGhlc2VfYXJlX2FsbF9pbnRlZ2VycyAweDY2LCAweDZjLCAweDYxLCAweDY3LCAweDdiLCAweDM4LCAweDczLCAweDc1LCAweDMzLCAweDZlLCAweDczLCAweDY4LCAweDVmLCAweDQ4LCAweDRmLCAweDRlLCAweDQ1LCAweDUzLCAweDU0LCAweDU5LCAweDVmLCAweDY5LCAweDczLCAweDVmLCAweDc0LCAweDY4LCAweDY1LCAweDVmLCAweDQyLCAweDY1LCAweDczLCAweDc0LCAweDVmLCAweDUwLCAweDZmLCAweDZjLCAweDY5LCAweDYzLCAweDc5LCAweDdkLCAweDBhCg==" | base64 -dthese_are_all_integers 0x66, 0x6c, 0x61, 0x67, 0x7b, 0x38, 0x73, 0x75, 0x33, 0x6e, 0x73, 0x68, 0x5f, 0x48, 0x4f, 0x4e, 0x45, 0x53, 0x54, 0x59, 0x5f, 0x69, 0x73, 0x5f, 0x74, 0x68, 0x65, 0x5f, 0x42, 0x65, 0x73, 0x74, 0x5f, 0x50, 0x6f, 0x6c, 0x69, 0x63, 0x79, 0x7d, 0x0a
On the name of the challenge I taught it was recursive zipped and which we would seen in many ctf already but this wasn’t the case here. We had zip file inside this given file we have to crack the password and get the flag.

I used zip2john to dump the hash of the zip file with password protected and used rockyou.txt to bruteforce the hash and got the password as pass123, on extracting you will get the flag.

We had a twitter account, which was joined in this month sept 2020 and it had image in reply tweet by mentioning another person. Who retweeted another person, where that account had instagram profile link and it had a image with todo list and that had the steghide password.
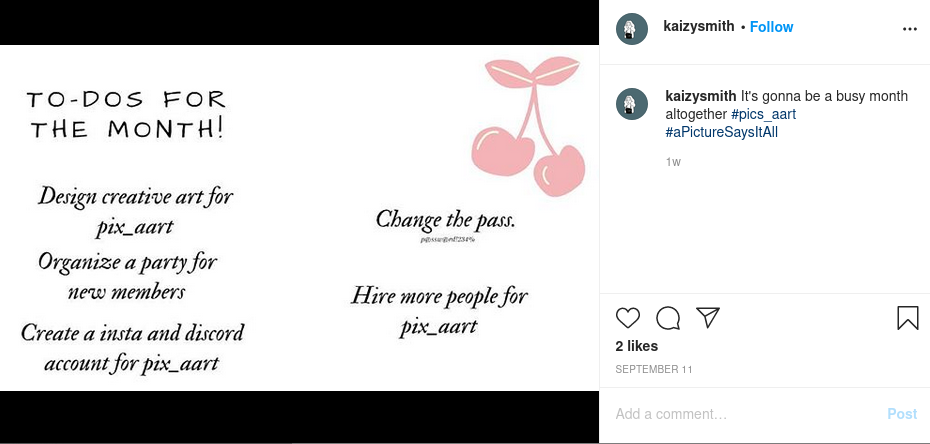
steghide extract -sf img.jpeg
Enter passphrase: p@ssw@rd!234%, wrote extracted data to "flag.txt".

This was one of the nice and cool challenge. We were given with a weblink again and it had same hidden comment here too. But this time the link was github repository and that had 4000+ commits and on looking into it, was just random folder and file creation and removal.

Tried Clone and looking into log and moving the head to respective commits and tried looking into the files, then create a python script for automated process even that did not work. But nothing worked actually then I taught, that I forgot about gitleaks. Then Figured the way for solution.

This gave output with one leak with commit message “folder_12/folder_7/file_5” then taught of using git and grep to figure out the hash for reset and we get 3 commit with same message. But one of them had the real flag in it.


We have next challenge with similar layout which we had before and it had comment tag for dnslookup tool from google, and we were given domain called winja.ctf and we have a ip address too.
On Port scanning the ip address, we came to know that it had 53 with Domain Name Server (DNS), and as the challenge name mentioned we need to dig for dns record for the flag. As usual to ctf scenario, flag might be present at AXFR record but port was filtered and by using dig command from local wasn’t connecting for me. So as they mentioned online tool.

with help of this “https://www.digwebinterface.com/?hostnames=winja.ctf&type=AXFR&useresolver=8.8.4.4&ns=self&nameservers=159.89.163.92”
LEVEL 3

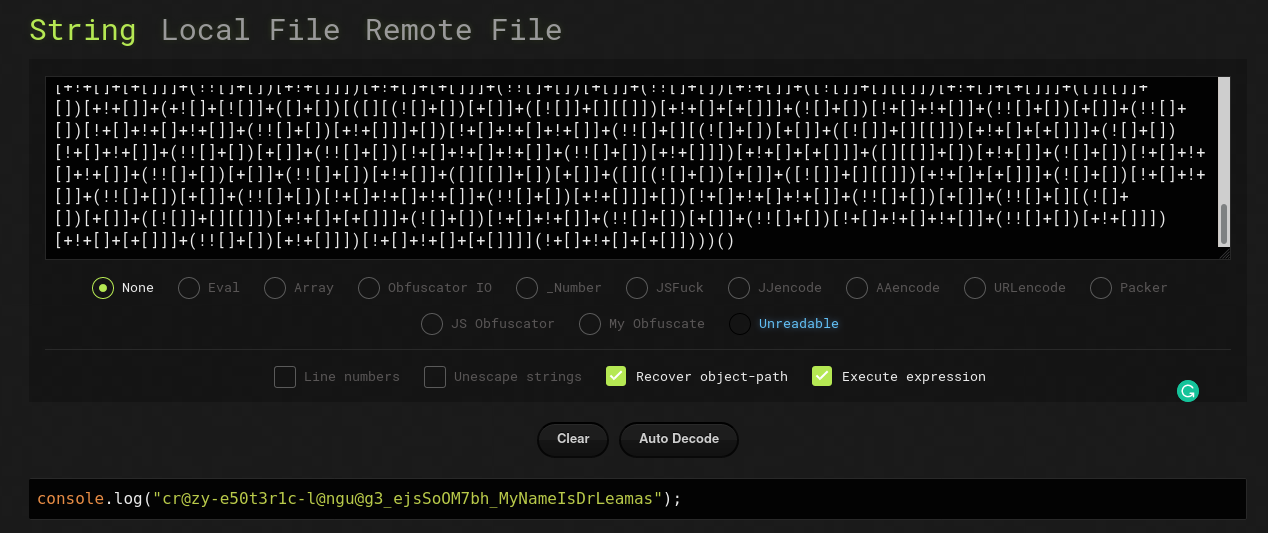
As the challenge itself gives the hint for the challenge its related to esoteric language and on downloading the file and looking into it we finalize it was a long JSFU*K language. Since this was a long one many did jsfu*k decoder online didnot work properly, but this one https://lelinhtinh.github.io/de4js/ made the job easier.

Here we have pcap file and challenge name “Jump the Shark” decodes the wireshark took for packet analysis. But before getting into wireshark I tried strings to check whether we had any flag. But we had a huge strings of flag matching with random mail and csrf_token which didnot work.

On analysis the string properly each was a request with random email and password as flag and csrftoken and it return code and message as response, we need to check for code:valid and message you logged in.
strings file.pcap | grep "\"code\":\"valid\""
which did not work for the case and then tried printing all string with valid substring we got a extra link with [email protected], which would be the flag for our challenge but submitting that did not give the correct for that challenge, tried decode it and submit since it was a hexdecimal number and we got the flag.


One of the simple classic BOF — Buffer overflow challenge. We were given with compiled c program file. Lets use radare2 to decompile and reverse engineering this file. We have a function called print_flag which we need and as executing the file we get to know that file is taking a input from user, we have to overflow the buffer to print_flag function to get the flag.

python -c "print 'A'*124 + '\xda\x50\x04\x00'" | ./a64.out
Above is the payload create to overflow the buffer and get the flag.
Next similar to jump the shark we have another pcap analysis forensics challenge. On similar way using strings reveal a lot of password with base64 strings which was like bruteforcing with rockyou.txt , No other go you have to use wireshark here. As it revealed the same, it was password cracking Scenario, but we had a new request for linux-virus.

This request had a elf file, but on looking here we have a secret string called 52c69e3a57331081823331c4e69d3f2e.THIS_IS_A_VIRUS which was a md5 hash and on reversing this with rockyou.txt
The MD5 hash:
52c69e3a57331081823331c4e69d3f2e
was succesfully reversed into the string:
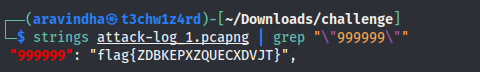
999999
Now lets look into the password base64 string for 999999 from strings of the file we get the flag.

We have a classic php challenge given here. On looking into the page we have upload feature and this did not restrict for any file, So upload a php reverse shell and got the flag. This was the challenge but shell broken the server and it wasn’t reacheable during this writeup, So try it by yourself for getting the flag. LAMO.


