DC9111 0x03 Safe Mode

Daddy Bits — Steganography
Challenge Description :
This is an old image that I recovered from my old Dad’s PC and I can’t see anything properly, I guess some bits have been manipulated and My Dad said it has a hidden message for Huge Treasure.

We get a jpeg file, you may try all string, steghide, binwalk and other stuff too but I guess you might missed jsteg.Use jsteg reveal Daddy_bits.jpg and we get link for file download https://mega.nz/file/bfBhzQ5A#i8WGbHF1K39wCxtnfW3yEBTiFPbRaUExY8KgG6JCy94

Its a png, lets again try binwalk zsteg strings but no results, Since description had a hint about bit manipulation and also but his dad so lets recon about it and we find a tool called appa in github and lets use to decode python3 appa.py -d Chall.png

We get some random hex digits and lets map out to xxd -r -p Chall.result and find out the file out and its also another png. Save that too Flag.png and open it just qr bar image. Lets scan and find it. But it returns Sorry No Flag here!! . lets check String or Exiftool, Comment in image has another link and it has the flag.

and the flag for the challenge is dc1111{1_l0v3_y0u_t00_B1t5}

Pickle Shell — PWN
Description:
You know all better than me just challenge name describes everything, if not google it
nc 52.147.195.39 45057
On connecting to the netcat connection, it says **Welcome to Pickle Shell!** which denotes were are on a shell.

when we try regular commands of linux machine it return on base64 string. when we decode it, some Garage value and which what command we tried.

From title lets decode with pickle base64 we get a hex string with delimiter as \x **\x80\x04\x95\x06\x00\x00\x00\x00\x00\x00\x00\x8c\x02ls\x94.**
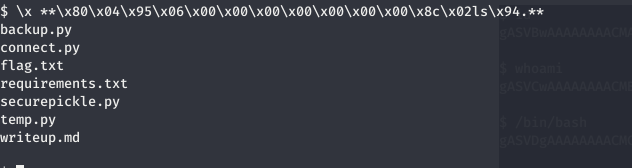
lets see which if we give base64 pickle string into to the shell and it return same string, as what we have made one with pickle decrypt. Lets make pickle according to its returning pickle string and lets test with this \x80\x04\x95\x06\x00\x00\x00\x00\x00\x00\x00\x8c\x02ls\x94.
And its executes the command and found a flag.txt out there, lets modify our command and pickle hex it and lets sent it.
Sending string \x80\x04\x95\x06\x00\x00\x00\x00\x00\x00\x00\x8c\x02cat flag.txt\x94. and BOOMMM we get the flag dc1111{p1Ck1iNg_s0m3_PiCklEs}

Shark Cry — Forencisc
Challenge Description :
We had recently undergo a ransomware attack and last week we restored all disk but I as a network analyst, Feel that there is some kind of malicious activity which is going in the background, So taught to run a tcpdump and got a PCAP file which has been attached below. Which has some random data frame requests which is transmistted within localhost subnet and to random port. I see some wired data transfer but all I can say is they follow some kind of pattern request where length of the data is also different and also nothing is clear text readable. Please help to remove this ransomware, Please dont tell me to pay ransom and get the key to resolve this.
Hint :
No of different packets might help you to decrypt.
Check the pattern and length of the data
First of all we have fix pcap file header change DD CC BB AA to D4 C3 B2 A1. then open file in wireshark and analyse

After Fixing the header, There are totally 7 different packet with order and repetation, they common data and each packet is either encrpyted in base64 or binary or clear text ascii.but when you check tcp packet, its payload length seems to be kind of sequence of numbers

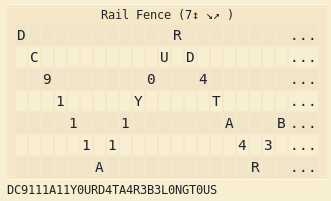
scrape it and put them under ascii to text and you will get “DRNCUD0G904LT1YT3011ABU1143SAR”.This is a railfence cipher with rows to 7 (From hint).This is a railfence cipher with rows to 7 (From hint) DC9111A11Y0URD4TA4R3B3L0NGT0US
Split the Sause — Web
Challenge Description:
My friend and I had a fight for Sauce packets, since we had only one sauce packet but two sandwich for our lunch. And finally we split the sauce into two equal half and we Shared #TrueFriendship.
Recommended:
* Use Curl then using Burpsuite
* Think out of the Box
Hint:
Make sure your content in binary format is Correct, and Check for the format also.
Pablo Escobar Inc has Launched another Phone.

This challenge is all about HTTP request smuggling. Here login or directory bruteforcing does not even matter. Just login and check homedirectory. Get the request, Remove all accepted encoding and add Transfer-Encoding to chunked and remove body data and replace with this :
0
GET /flag HTTP/1.1
Host: 0.0.0.0:45054convert this into a Curl request and get the flag.

for More info : https://portswigger.net/web-security/request-smuggling/exploiting
Triple Rotten — Programming
Challenge Description :
My friend gave this file which prints something with some random character with all same length and some list of number with some number. I guess you can understand this, Can you help me to solve this. and He said to remerber the word triple which may denotes THREE or TROIS or TRE or 3.
Hint :
Not only strings can be rotated even lists can be rotated
Files: chall.py output.txt
Just analyse the code you will find function called prime and number which is used just to find least prime number from given number 28101276533935461337993.Print the least prime and check it would be returing the number 3. Comment out those number function so that result is printed out immediately, as per program and output it just rotates the flag with length of printable array and list of number and index of each index which is from 0–2 (Which is less than 3)
The Number in front of each array denotes no of rotation that are made before, so do the opposite rotation to get original position.Now list has 3 arguments which denotes which index of flag, which lines in above and character from respective array. Join all character into a single string and you will get a rotten string again.
As per title/description its encrypted with ROT3 so decrypt with ROT23 and we get the flag “dc1111{Pyth0n_1nd3x1s@w3s0me_Alw@y$}”
For Challenge files and Writeup :


