Winja - C0C0N 2021

Winja CTF at C0C0N 2021 was 15 hours long CTF with 20+ challenges in various categories. Like other CTF, we also faced hurdles in beginning with infrastructure issues but once the event kicked off it was a smooth run. We had around 700+ users register and 450+ teams playing across the globe.
We as CTF moderate were available throughout the CTF time in discord in text and voice chat to handle challenge issues and server.
Reciprocal Cipher
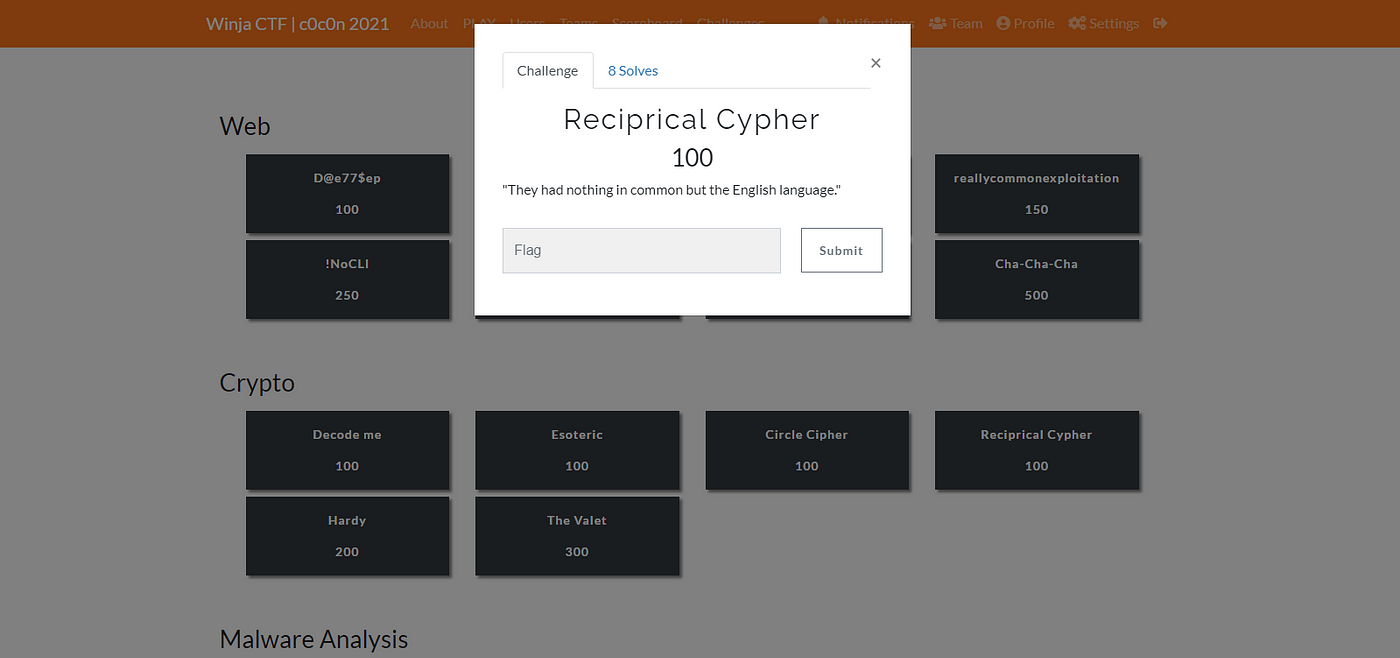
Description: It's not Chinese or Koireng Language, just English try to Decode if possible.
Difficulty: Easy
Category: Crypto
Point: 100
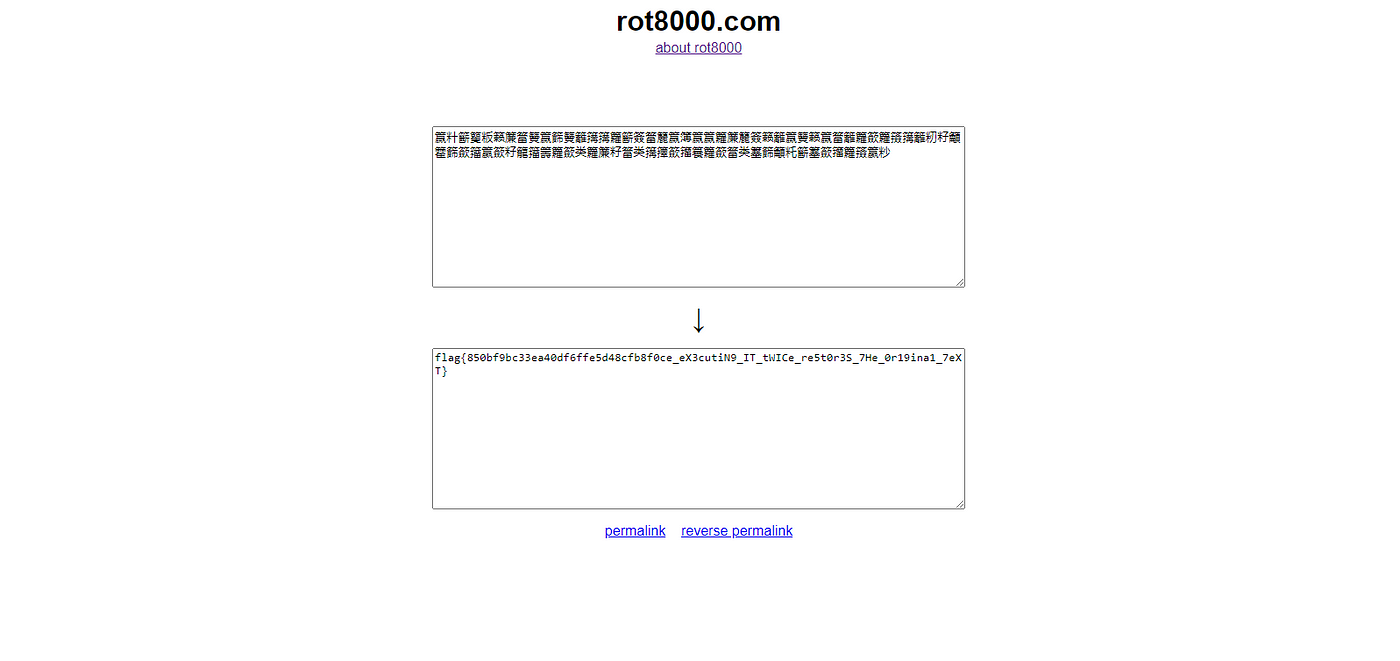
This was actually a file, but when you look through the Nginx proxy should be different. So you should save it and then process it. The hint was given later during CTF as a “Famous cipher with higher value”. This might look like Chinese but when you try to translate you will get similar text in English which is kind of weird.

It's just Unicode character and it's called Reciprocal Cipher which means when you encrypt text twice you will get plain text. It's Caesar cipher or ROT with value 8000. https://rot8000.com/Index
BlogQL

Description: We have made a secure blog posting platform for our l33t which is powered by new Tech called BlogQL. For Querying blog information without any limits.
Difficulty: Medium
Category: Web
Point: 250

This is how the landing page looks like which has two main blogs, one about some query language and another about Hasura which is a backend service that uses graphql. We also have a login page for authors, when you try to enter any username and password, you will see a fishy request from the client to the endpoint called graphql.

you will see two graphql requests, one for verifying the login username and password, and the second one pulls the login information and validates it client side. Which gives the lead to login into the account. Once you login in that should have information about private blogs.
So we have graphql endpoint and private blogs. hence we construct a graphql query to pull those private blogs.

When you try introspection query, you will find a schema object called secret blogs is found here, Now you have to fetch all records inside the database and it will give you the flag.
query {
secretblogs {
title
content
}
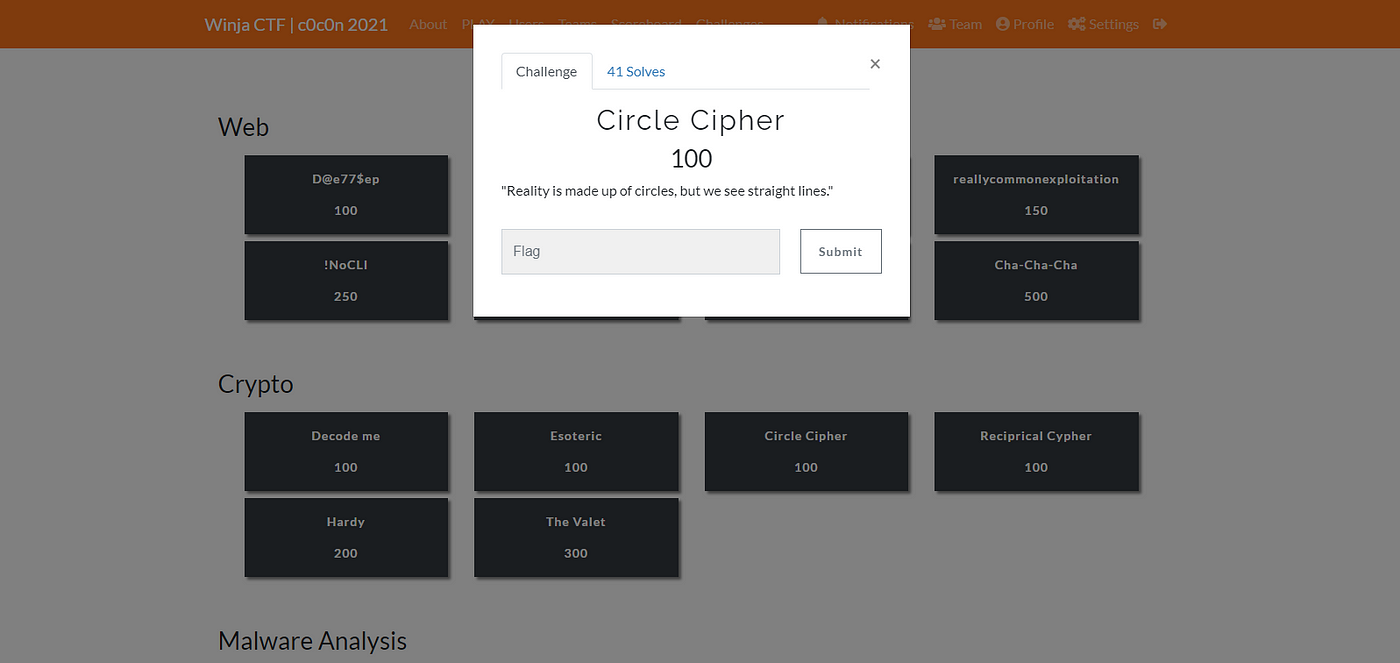
}Circle Cipher
Description: Get some pencils with a compass and scale to draw a few circles with verticles lines to create a wonderful glyph.
Difficulty: Easy
Category: Crypto
Point: 100

It was a pdf file that had this encrypted text using some random circle and line symbols. When you try reverse image search or google it as circle cipher will not definitely get it. And some results might be leading to the Ceaser cipher. But since this was the old way of encryption.
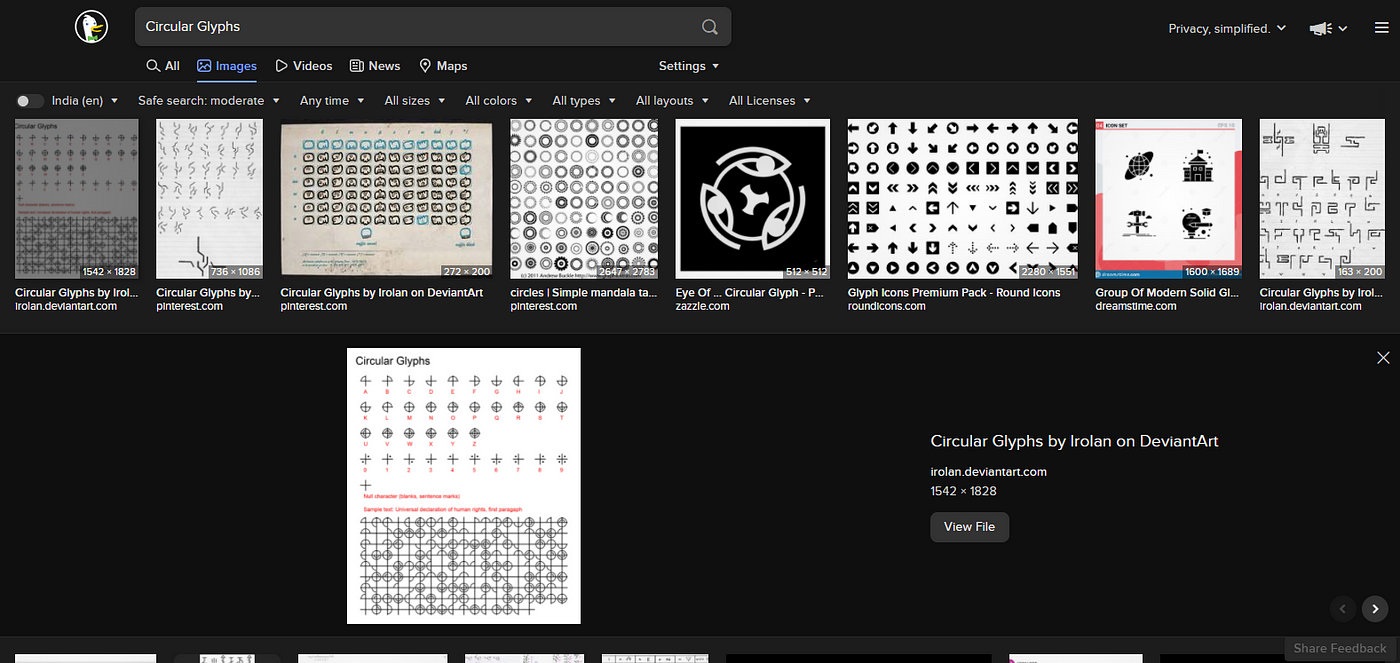
When you decode it manually you will find the flag.
The Valet
Description: AES — Advanced Encryption Standard, It’s already broken so You can also break it.
Difficulty: Medium
Category: Crypto
Point: 250

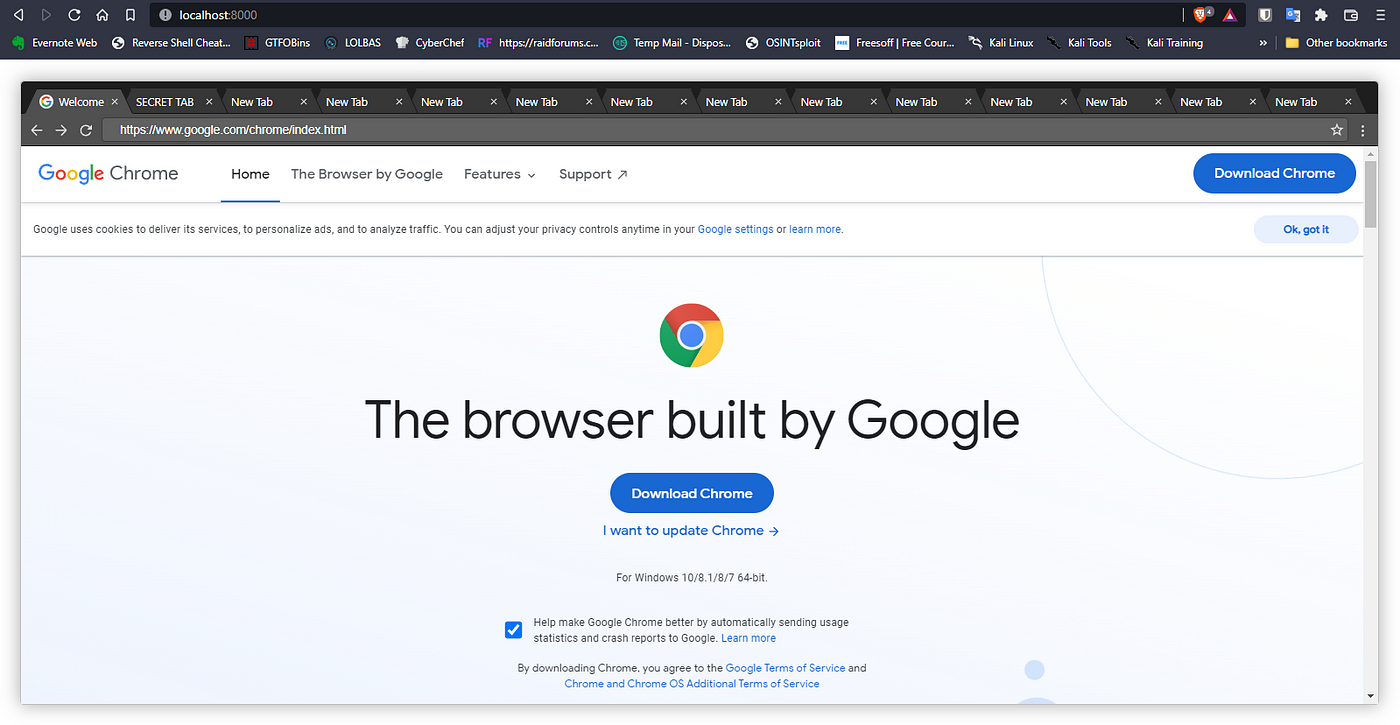
It was a Web challenge and we had a landing page with a google chrome website. It looks similar to a chrome browser with 20 tabs already opened, and one among them had a tab named “Secret Tab” which had a hint to use dirbuster.
You will find a hidden directory called .secret which will have three files, one with a hint to solve this challenge by decrypting the chrome password manager with help of an unprotected secret key.
import json, base64
import sqlite3
from Cryptodome.Cipher import AES
secret_key = base64.b64decode()
conn = sqlite3.connect("Login Data")
cursor = conn.cursor()
cursor.execute("SELECT action_url, username_value, password_value FROM logins")
for index, login in enumerate(cursor.fetchall()):
url = login[0]
username = login[1]
ciphertext = login[2]
if url != "" and username != "" and ciphertext != "":
try:
initialisation_vector = ciphertext[3:15]
encrypted_password = ciphertext[15:-16]
cipher = AES.new(secret_key, AES.MODE_GCM, initialisation_vector)
decrypted_pass = cipher.decrypt(encrypted_password)
decrypted_pass = decrypted_pass.decode()
decrypted_password = decrypted_pass
except Exception as e:
print(e)
print("URL: %s\nUser Name: %s\nPassword: %s\n"% (url, username, decrypted_password))
cursor.close()
conn.close()Hash Map
Description: HashMap can get the right value if you have the right key
Difficulty: Medium
Category: Reverse Engineering
Point: 200

Hashmap is like all reverse engineering in other CTF, which were given with executable binary. But strings or other tools did not help to find clear text inside the binary.

Opening the binary in any debugger like IDA, Ghidra, or Binary Ninja we will find your main function in the problem. one is the main function which takes a user input and sent as a parameter to another function called check password which is consist of nested if-else check condition.
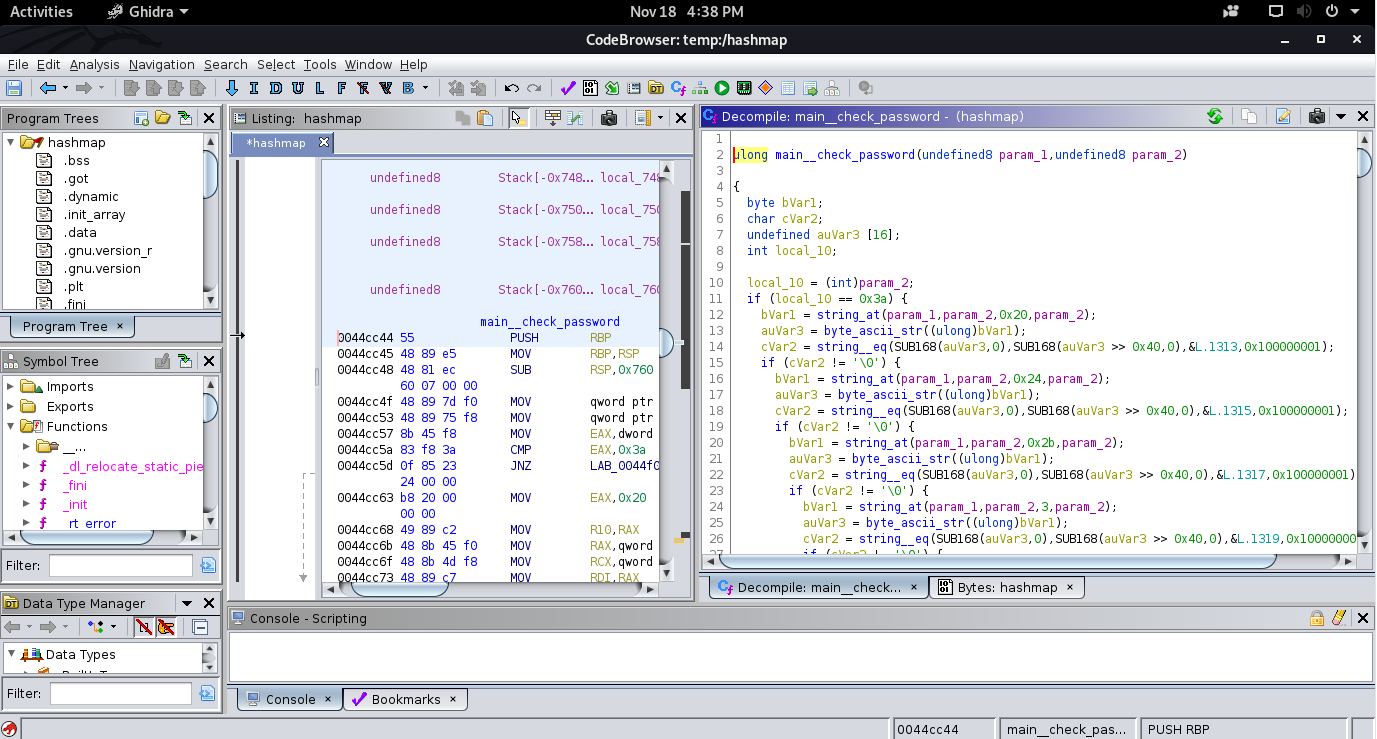
On Closing watching, you will find it checks each character of the password to another value, which is mapped to the index in the actual flag. So you have to decode the value and put it in the respective index value to get the flag.
Believe Your Eyes
Description: Look twice or thrice
Difficulty: Easy
Category: Steg
Point: 100

This was one of the easiest challenges in this CTF which has an image with three different parts of CTF hidden inside RGB planes of the image. You can use a tool called Stegsolve to get the flag.
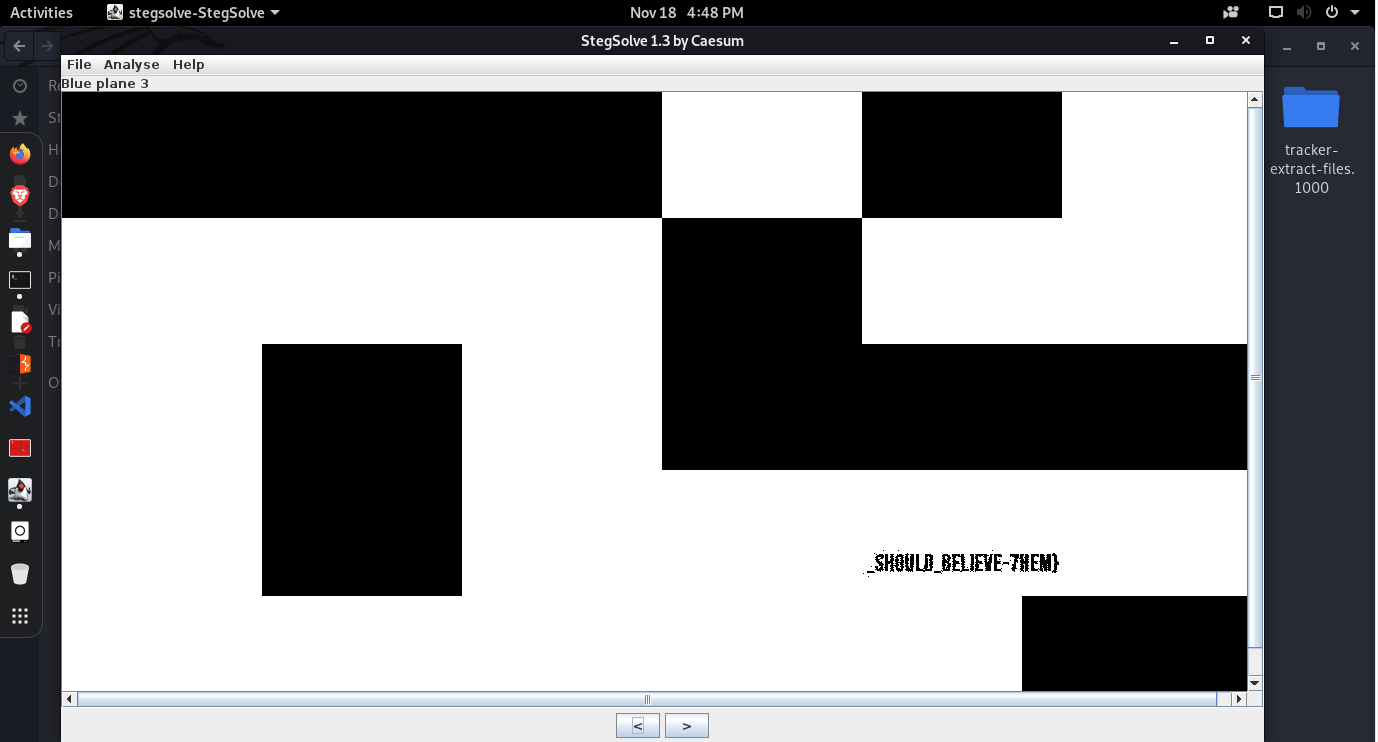
Thanks for Reading this CTF write-up till the end, hope you enjoyed the challenges.


